Trezor Login — How Access and Authentication Work
This page explains the practical meaning of “login” when using a Trezor hardware wallet and companion software. It describes device-based authentication, PINs and optional passphrases, local protections, transaction confirmation, troubleshooting, and recommended best practices for secure access.
Fundamental concept: device as credential
With a hardware wallet, the central credential is the device itself. The device holds the cryptographic private keys inside a tamper-resistant element and never exposes them to the host computer. In practical terms, “logging in” to a wallet interface means connecting the hardware device to the host environment and unlocking it locally on the device using a PIN. The host application provides a user interface, but the hardware device remains the authoritative source for signing transactions and authorizing sensitive operations.
PIN: local unlock, not a server password
The device PIN is a local security control that prevents unauthorized use of a physical device. The PIN is entered on the host device or, when supported, directly on the wallet screen. A correct PIN unlocks the device for a finite time window and allows the user to view accounts and sign transactions. The PIN protects physical possession; it is not a remote authentication credential and is not transmitted to or stored by any server.
Optional passphrase (25th word) and advanced access
Beyond the basic PIN, an optional passphrase can be enabled as an additional secret. When used, the passphrase is combined with the device seed to derive distinct wallets. This feature provides plausible deniability or the ability to manage multiple independent wallets from one device. A passphrase is a sensitive secret: if used, it must be entered carefully and stored securely, because loss of the passphrase can render funds unrecoverable. The passphrase is strictly local and is never requested or stored by external software.
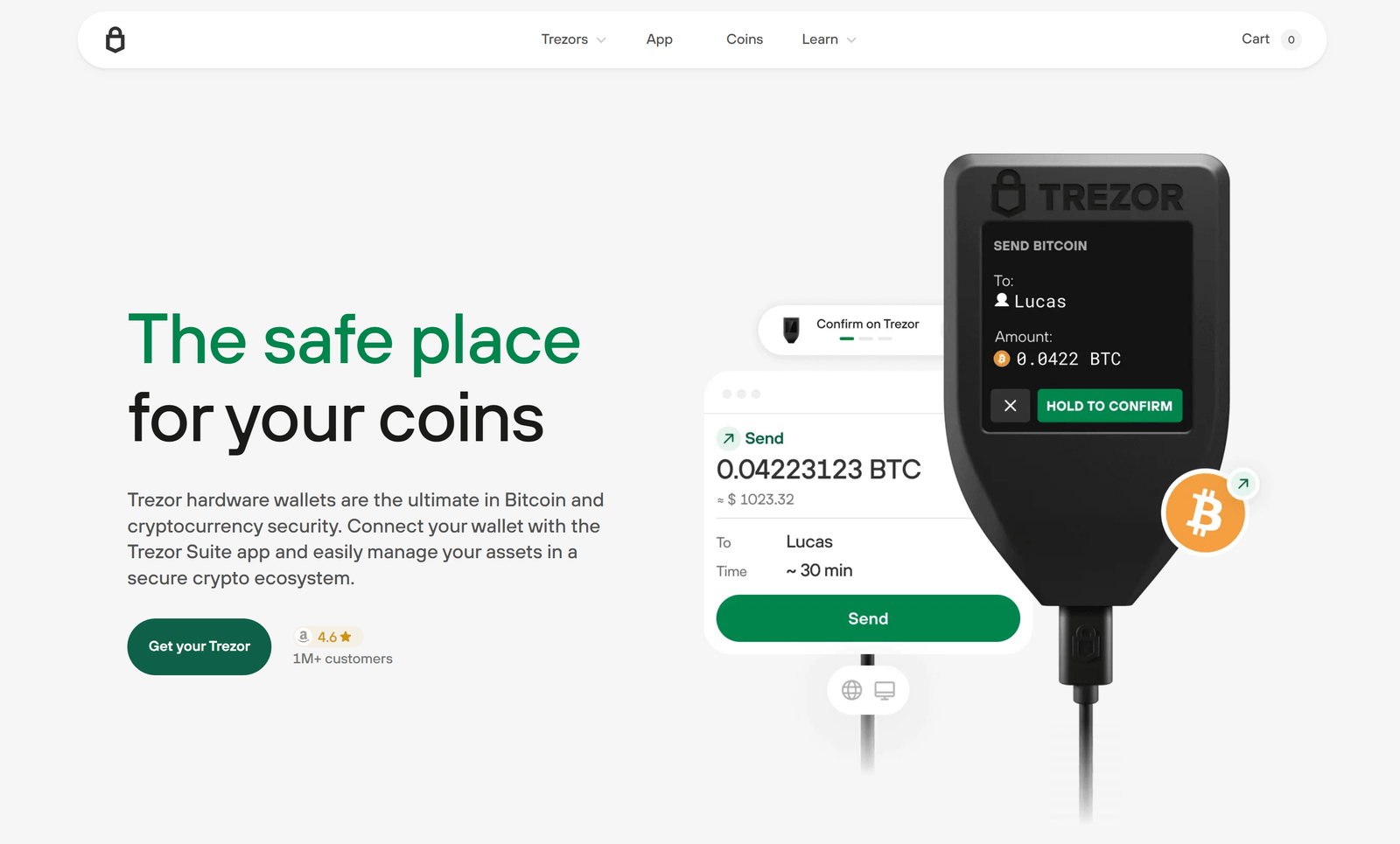
On-device confirmation and transaction integrity
Important security decisions require explicit on-device confirmation. When initiating a transfer or interacting with a contract, the host application constructs a transaction and transmits it to the device for signing. The device displays human-readable information such as destination address and amount, and the user must confirm the details on the device before signing occurs. This model prevents the host environment from silently authorizing transfers without the user’s knowledge.
Local application protections
Companion applications may offer local protections such as a password lock or encrypted local storage to reduce casual exposure of account metadata on a host computer. These controls are convenience features and do not replace the device’s hardware security model. In every case, the private keys remain on the device, and only signed transactions leave it.
No server-side login or custodial access
Interacting with a hardware wallet does not involve a centralized login system where credentials are stored on a remote server. There is no vendor-managed account that can access funds on behalf of a user. This non-custodial model ensures the user retains full control over asset custody, but it also places responsibility on the user to secure recovery materials and to follow sound operational procedures.
Practical access flow (informational)
Typical access proceeds as follows: connect the hardware device to the host, unlock the device with the PIN, open the companion application (desktop or browser interface), and open the relevant on-device application for the blockchain in use. The host application synchronizes account data and displays balances. Any transaction requires device review and explicit approval on the device before it is broadcast to the network.
Recovery phrase and account restoration
Recovery uses a written phrase generated by the device during initialization. This phrase is the authoritative backup and must be recorded offline. Restoration on a new device requires the recovery phrase and, if applicable, any passphrase used. Never enter a recovery phrase into a host computer or application except when restoring on a verified hardware device as part of an authenticated, local recovery flow.
Troubleshooting access issues
Access problems are often caused by cable or connection issues, device firmware mismatch, or host software version incompatibility. Simple checks include verifying the cable and port, confirming the device screen prompts, ensuring firmware is current, and using a supported companion application. If hardware PINs are forgotten, the only recovery path is the recovery phrase; there is no vendor reset that reveals private keys.
Best practices for secure access
- Record and protect the recovery phrase in multiple secure, offline locations.
- Use a strong PIN and consider a passphrase only if you understand its implications.
- Always verify transaction details on the device screen before approving.
- Keep device firmware and companion software up to date using official update procedures.
- Use local application locks to prevent casual access to account metadata, but do not rely on them for custody protection.